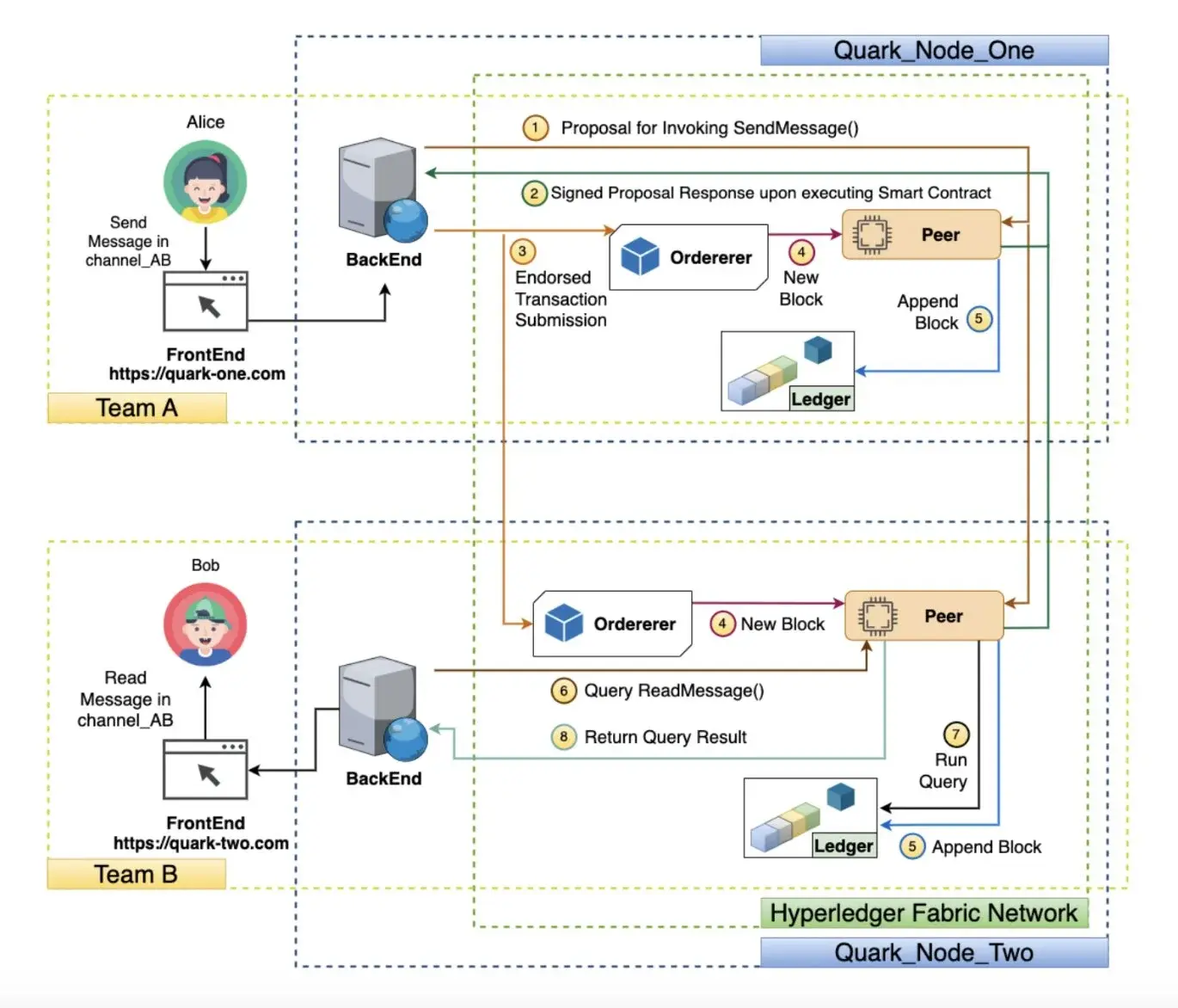
Researchers from several institutes worldwide recently developed Quarks, a new, decentralized messaging network based on blockchain technology. Their proposed system could overcome the limitations of most commonly used messaging platforms, allowing users to retain control over their personal data and other information they share online.


I believe their point was that even encrypted messages convey data. So if you have a record of all the encrypted messages, you can still tell who was talking, when they were talking, and approximately how much they said, even if you can’t read the messages.
If you wait until someone is gone and then loudly raid their house, you don’t need to read their messages to guess the content of what they send to people as soon as they find out. Now you know who else you want to target, despite not being able to read a single message.
This type of metadata analysis is able to reveal a lot about what’s being communicated. It’s why private communication should be ephemeral, so that only what’s directly intercepted can be scrutinized.
That was exactly why I said “Did they learn nothing from the Obama administration?”
From 2014: “We kill people based on metadata.” (Michael Hayden, former DIRNSA, 2014.ev)
There is no “harmless” here.
But in this case, the metadata is not accessible to outsiders.
If you can see it, you can analyze it. Metadata is more than message headers; traffic analysis generates usable metadata, too.
Any form of internet communication is potentially susceptible to traffic analysis, so that flaw isn’t specific to this particular design.
The goals here are to address some of the other weaknesses of communication protocols, ie lack of auditability and reliance on a central server. They do not claim it’s completely impervious to attack.